iOS 18.2 introduces Image Playground, a revolutionary AI app for creating unique images directly on your iPhone. Explore its features, benefits, and creative...
Author - Stacy Cook
![]() Stacy earned a B.S. in Computer Science with coursework in cybersecurity. She has 7 years of experience covering cloud platforms, AI tooling, enterprise software, and developer ecosystems. She is known for change log breakdowns and hands on explainers that help readers adopt new tools safely. She has guest judged university hackathons and mentors early career reporters on technical sourcing. Stacy climbs indoor routes, enjoys indie games, and keeps a home lab for testing. She writes the daily tech brief, coordinates product deep dives, and maintains our glossary of technical terms.
Stacy earned a B.S. in Computer Science with coursework in cybersecurity. She has 7 years of experience covering cloud platforms, AI tooling, enterprise software, and developer ecosystems. She is known for change log breakdowns and hands on explainers that help readers adopt new tools safely. She has guest judged university hackathons and mentors early career reporters on technical sourcing. Stacy climbs indoor routes, enjoys indie games, and keeps a home lab for testing. She writes the daily tech brief, coordinates product deep dives, and maintains our glossary of technical terms.
Avalanche CEO proposes freezing Satoshi's Bitcoin amid quantum computing concerns. Is this a necessary precaution or a threat to Bitcoin's decentralization?
T-Mobile launches new 5G Home Internet plans with Price Lock, no contracts, and unlimited data. Learn more about Rely, Amplified, and All-In plans.
Will Ethereum outperform Bitcoin? Bybit explores the factors driving ETH's potential surge, including The Merge, DeFi growth, and NFT boom.
The OnePlus Watch 3 is rumored to feature a larger battery for extended use, addressing a key limitation of its predecessor. Learn more about the potential...
OpenAI launches ChatGPT Pro, a $200/month subscription service offering advanced AI tools for research. Learn about its features, benefits, and potential...
Discover why Apple is sticking with a titanium chassis for the iPhone 17 Pro models, defying rumors of a switch to aluminum, and what this means for users and...
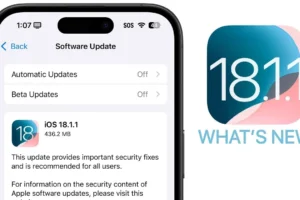
Discover what's new in the Apple iOS 18.1.1 update. Important security updates and enhanced features ensure your iPhone runs smoother and safer.
Discover how the $13.6 billion Bitcoin options expiry could influence BTC's climb to $100K. Analysis of market trends, options dynamics, and expert predictions.
Microsoft warns 450 million Windows users of critical vulnerabilities exploited by hackers. Essential updates and security practices are urgently recommended.